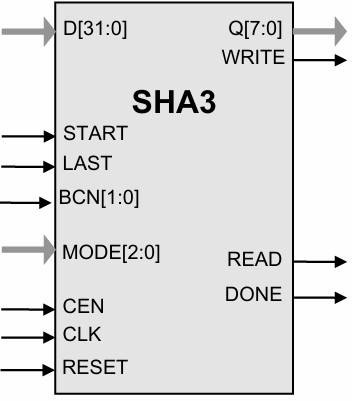
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
| IP Cores, Inc., 3731 Middlefield Rd., Palo Alto, CA 94303, USA | Phone: +1 (650) 815-7996 | E-mail: [email protected] | www.ipcores.com |
| Copyright © 2008- , All Right Reserved, IP Cores, Inc. | Home | About Us | News | Contact Us | Privacy Policy | Export Information |